From seamless infrastructure setup to advanced firmware development.
The only tech partner managing your business growth, bit by bit.
Finally! Space to breathe.
































































Deploy our autonomous agents to scan your infrastructure, exposing critical vulnerabilities and hidden cost inefficiencies.
The future of Cybersecurity is here. Ditch obsolete legacy tech. We secure your business infrastructure with SentinelOne Singularity™, the market-leading XDR solution.
Advanced Capabilities
Autonomous PreventionBlock zero-day threats and unknown malware before they cause damage.
Instant RollbackRestore encrypted files with a single click.
Fully Managed ServiceConfiguration, monitoring, and incident response handled entirely by our SOC experts.
Total VisibilityExtended protection across all corporate endpoints.
Lightweight AgentA single agent that never slows down system performance.
We work with passion and expertise to provide high-quality products, always aligned with our clients' needs.
Are you looking for uncompromising security and reliability? We design custom digital infrastructures that reduce costs and technical risks. Discover the perfect solution for your business.
Dedicated technicians at your service.
Response within 5 minutes.
A security-first MSP.
We build a relationship of trust.
We developed a distributed threat intelligence system analyzing millions of malicious IPs in real-time. A technical case study on architecture, automation, and applied network security.
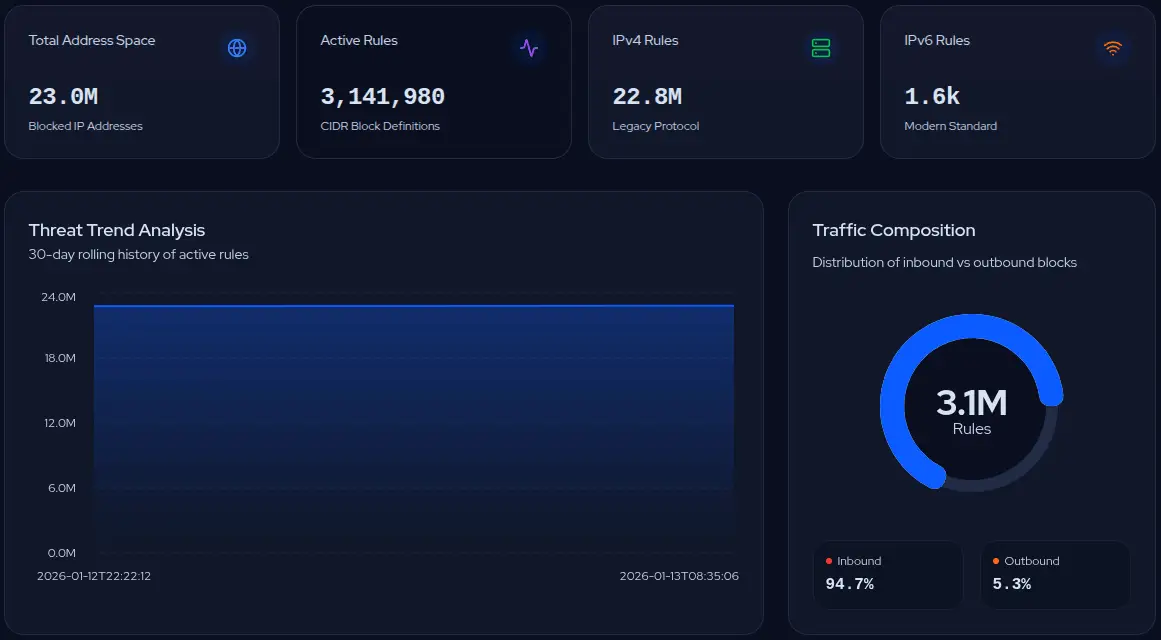
20M+
Blocked IPs
24/7
Real-time blocklist sync
99%
Less background noise
Global
Infrastructure coverage
Every server exposed on the Internet undergoes thousands of scanning attempts daily. It's not a matter of "if", but "how much". Automated bots, opportunistic scanners, and malicious actors continuously test open ports, known vulnerabilities, and weak configurations. This hostile traffic generates three critical problems:
For this project, we implemented a multi-source approach that overcomes the limitations of traditional static blacklists:
The result is a fully automated system: the blocklist updates every 120 minutes, autonomously adapting to the evolving threat landscape without requiring manual intervention.
| KPI | Standard Firewall | With Bitwire Grid |
|---|---|---|
| Port Exposure | Total (Continuous scans) | Selective (Clean IPs only) |
| Log Analysis | Difficult (Too much noise) | Clean and readable |
| Rule Updates | Manual / Slow | Automatic (Real-time) |
While most solutions focus only on incoming traffic, we implemented a bidirectional approach:
Ingress Filtering: Blocks scanners, brute-force, and exploits before they reach your services.
Egress Protection: Even in the event of a system compromise (e.g., via a zero-day), malware cannot communicate with Command and Control (C2) servers. Egress Guardrails intercept and block "phone home" calls, preventing data exfiltration and remote control.
“We built this system starting from a principle: modern threats are automated and constantly evolving. The only effective defense is a system that adapts at the same speed as the attackers, without requiring human intervention.”
Through this project, we demonstrated how a well-designed threat intelligence system can produce measurable results:
This project demonstrates how intelligent automation can transform perimeter defense from reactive to proactive, making infrastructures invisible to opportunistic attacks.

Executive Summary
An open source project developed by Bitwire to demonstrate the practical application of automated threat intelligence. The system analyzes over 20 million malicious IPs in real-time, reducing hostile traffic by 99% and improving visibility of real threats.
Industry
Network Security / SaaS
Open Source
GithubExplore the Project
View Live Statistics